|
Preface
The role of a Microsoft security operations analyst is essential in ensuring that the organization's information technology systems are secure from any possible threat. This is achieved through collaboration with various stakeholders in the organization to assess the risk levels and determine the necessary measures to mitigate them.
One of the primary responsibilities of the security operations analyst is to monitor and respond to any potential threats within the environment.
This is done through the use of various security solutions, including Microsoft Sentinel, Microsoft Defender for Cloud, Microsoft 365 Defender, and third-party security products.
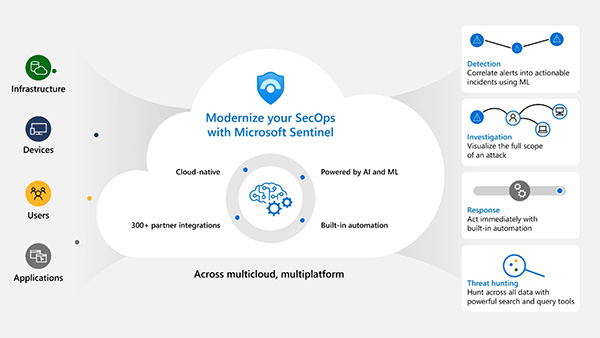
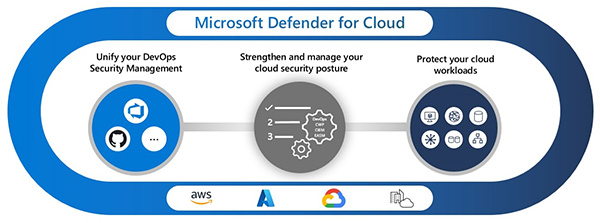
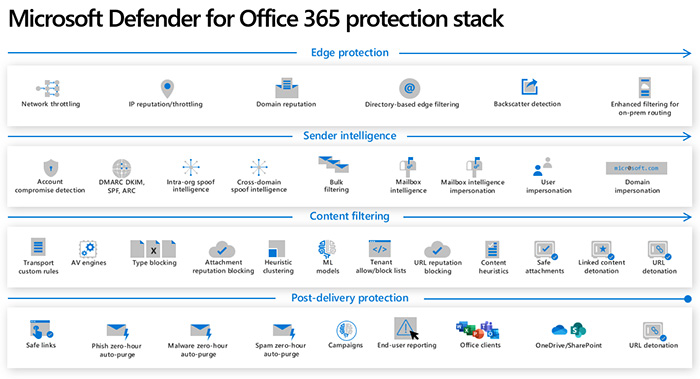
The security operations analyst should be highly experienced, practiced, skilled and very knowledgeable in these above tools' operation to effectively utilize them to secure the organization's systems.
In addition to responding to threats, the security operations analyst should also identify areas for improvement in threat protection practices.
This includes analyzing data from security solutions and using it to advise on changes to security practices, policies, and procedures. If any violations of organizational policies are detected, the security operations analyst should refer them to the appropriate stakeholders for further action.
To be successful in this role, candidates should have knowledge of various attack vectors and cyber threats, as well as incident management.
They should also be proficient in using Kusto Query Language (KQL), which is a query language used to analyze data in Azure Log Analytics and Azure Application Insights.
Moreover, candidates should have a good understanding of Microsoft 365 and Azure services to be able to consume the operational output of the security tools.
Overall, the role of a Microsoft security operations analyst is critical in ensuring the organization's information technology systems are secure from potential threats. Their ability to rapidly respond to active attacks and identify areas for improvement in threat protection practices is key to reducing organizational risk.

Microsoft Certified Security Operations Analyst Associate
The Certification “Microsoft Certified Security Operations Analyst Associate” validates your capability to implement security controls and threat protection, manage identity and access, and protect data, applications, and networks in Azure cloud, Microsoft 365 and multi-cloud environments as part of your global infrastructure.
About the course
Our training course will guide you through carefully selected exam topics, along with real-life examples, practical demonstration and business cases of implementing, verifying and maintaining various Microsoft Sentinel, Defender for Cloud and Defender for M365 Security features.
Evaluations, Pros and Cons and may be comparisons of various Microsoft Security products would be verbally provided throughout the training course.
As Microsoft has been partnering with multiple 3rd party vendors and built security-related ecosystems, it is inevitable that a small portion of the course time would be spent on briefly discussing popular partner security solutions.
Our senior instructor Mr. Larry Chan would give you advise, tricks and tips on various cloud security-related products.
|




