(在家觀看 = 0%,在校觀看 = 100%)
100% 在校觀看日期及時間:
自由選擇,點選以下地區觀看辦公時間及位置
課時: 42 小時
享用時期: 21 星期。進度由您控制,可快可慢。
課堂錄影導師:Franco
在校免費試睇:首 3 小時,請致電以上地點與本中心職員預約。
本課程提供在校免費重睇及導師解答服務。
(在家觀看 = 100%,在校觀看 = 0%)
100% 在家觀看日期及時間:
每天 24 小時全天候不限次數地觀看
課時: 42 小時
享用時期: 21 星期。進度由您控制,可快可慢。
課堂錄影導師:Franco
在校免費試睇:首 3 小時,請致電以上地點與本中心職員預約。
本課程提供導師解答服務。
華為是全球領先的資訊與通信技術 (ICT) 解決方案供應商。華為的產品覆蓋了企業網路、電信網路、雲計算和物聯網等領域,為全球無數用戶提供服務。眾多企業均採用華為的產品和解決方案,因此,掌握華為網路設備的管理技術成為一項重要的專業技能。
為了證明你具備專業水準來安裝、配置及管理華為的網路產品,華為推出了 HCIA-Datacom (Huawei Certified ICT Associate - Datacom) 國際認可證書考試。本中心的 HCIA-Datacom 課程由經驗豐富的網路專家精心設計,課程內容涵蓋考試大綱。課程包括課堂講授、課堂實習、考試研習和模擬試題等環節,為你量身打造一個系統化的學習過程,助你快速而有效地取得認證。
| 課程名稱: |
HCIA-Datacom (Huawei Certified ICT Associate - Datacom) 國際認可證書課程 - 簡稱:HCIA Datacom Training Course |
| 課程時數: | 課堂 42 小時 (共 14 堂) |
| 適合人士: | 對電腦網路安裝及使用有基本認識或有志投身 I.T. 界的人士 |
| 授課語言: | 以廣東話為主,輔以英語 |
| 課程筆記: | 本中心導師親自編寫英文為主筆記,而部份英文字附有中文對照。 |
| 1. Franco Tsang (CCIE #19772) 親自教授: | Franco 具備三項 CCIE 認證 (Routing and Switching、Security 及 Service Provider),並有教授網路認證課程的極豐富經驗。 |
| 2. Franco Tsang 親自編寫筆記: | Franco 親自編寫筆記,絕對適合考試及實際管理網路之用,令你無須「死鋤」如字典般厚及不適合香港讀書格調的書本。 |
| 3. 提供模擬考試題目: | 本中心為學員提供模擬考試題目,每條考試題目均附有標準答案。而較難理解的題目,均會附有導師的解釋。 |
| 4. 快速取得認證: | 本中心的 HCIA-Datacom 時數合共 42 小時,教授考試內容及於課堂內實習最重要的項目,令學員有效學習和掌握知識。 |
| 5. 免費重讀: | 傳統課堂學員可於課程結束後三個月內免費重看課堂錄影。 |
只要你於下列科目取得合格成績,便可獲頒 HCIA-Datacom 國際認可證書:
|
本中心為Huawei指定的 HCIA-Datacom 考試試場,報考時請致電本中心,登記欲報考之科目考試編號、考試日期及時間 (最快可即日報考)。 臨考試前要繳付考試費 HK$1,640,及必須出示下列兩項有效之身份證明文件,否則考生不可進行考試,而已繳付之考試費亦不會退回: 考試題目由澳洲考試中心傳送到你要應考的電腦,考試時以電腦作答。所有考試題目均為英文,而大多數的考試題目為單項選擇題 (意即 O) 或多項選擇題 (意即 口),其餘則為配對題。作答完成後會立即出現你的分數,結果即考即知!考試不合格便可重新報考,不限次數。欲知道作答時間、題目總數、合格分數等詳細考試資料,可瀏覽本中心網頁 "各科考試分數資料"。 |
| 課程名稱:HCIA-Datacom (Huawei Certified ICT Associate - Datacom) 國際認可證書課程 - 簡稱:HCIA Datacom Training Course |
1 Data communication and network basics
1.1 Network communication concepts
1.2 Information Transfer Process
1.3 Common Terms
1.4 Concept of the Data Communication Network
1.5 Switches
1.6 Routers
1.7 Firewall
1.8 Wireless devices
1.9 Network Types and Topology Types
1.9.1 LAN, MAN, and WAN
1.9.1.1 Local Area Network (LAN)
1.9.1.2 Metropolitan Area Network (MAN)
1.9.1.3 Wide Area Network (WAN):
1.9.2 Network Topology
1.9.3 Network Topology Types
1.10 Network Engineering and Network Engineers
1.10.1 Network Engineering
1.10.2 Network Engineer
1.11 Network Reference Model and Standard Protocols
1.11.1 OSI Reference Model
1.11.2 TCP/IP Reference Model
1.11.3 Common TCP/IP Protocols
1.11.4 Common Protocol Standardization Organizations
1.11.5 Common Application Layer Protocols
1.11.6 Common Transport Layer Protocols
1.11.6.1 TCP and UDP - Port Numbers
1.11.6.2 TCP Connection Setup - Three-Way Handshake
1.11.6.3 TCP Sequence Number and Acknowledgment Number
1.11.6.4 TCP Window Sliding Mechanism
1.11.6.5 TCP Shutdown - Four-Way Handshake
1.11.7 Network Layer Protocols (e.g., IPv4)
1.11.8 Data Link Layer Protocols
1.11.8.1 Address Resolution Protocol (ARP)
1.11.8.1.1 ARP Cache
1.11.8.1.2 ARP Request Process
1.11.8.1.3 ARP Reply Process
1.11.9 Data Encapsulation and Decapsulation
1.11.9.1 Data Encapsulation on the Sender
1.11.9.2 Data Decapsulation on the Receiver
2 Build an IP network with interconnection and interworking
2.1 Versatile Routing Platform (VRP)
2.1.1 Introduction to Versatile Routing Platform (VRP)
2.1.2 File System
2.1.3 Storage Media Overview
2.1.4 Device Initialization Process
2.1.5 Device Management
2.1.6 VRP User Interfaces
2.1.7 CLI - Local Login
2.1.8 Basic Command Structure
2.1.9 Command Views
2.1.10 Editing a Command
2.1.11 Using Command Line Help / Using Command Line Online Help
2.1.12 Interpreting Command Line Error Messages
2.1.13 Using Undo Command Lines
2.1.14 Using Command Line Shortcut Keys
2.1.15 File and Directory Management in VRP
2.1.16 Basic Configuration Commands
2.1.16.1 System name, time zone and date time
2.1.16.2 User Interface Management
2.1.16.3 Configuring IP Addresses on Interfaces
2.1.16.4 Configuration Management
2.1.16.5 Saving and Managing Configuration Files
2.2 Network Layer Protocols and IP Addressing
2.2.1 Network Layer Protocols
2.2.1.1 IP Packet Header Information
2.2.1.2 Data Packet Fragmentation
2.2.1.3 Time to Live (TTL)
2.2.2 IP Addressing
2.2.2.1 IP Address Notation
2.2.2.2 IP Address Structure
2.2.2.3 IP Address Classification (Classful Addressing)
2.2.2.4 IP Address Types
2.2.2.5 Private IP Addresses
2.2.2.6 Special IP Addresses
2.2.2.7 Subnetting
2.2.2.8 Network IP Address Planning
2.2.3 Internet Control Message Protocol (ICMP)
2.2.3.1 ICMP Redirection
2.2.3.2 ICMP Echo Messages
2.2.3.3 ICMP Error Messages
2.2.3.4 Tracert / Traceroute Utility
2.3 IP Routing Basic
2.3.1 Routes
2.3.2 Routing Information
2.3.3 IP Routing Table
2.3.4 How to Obtain Routing Information
2.3.5 Direct Routes
2.3.6 Route Preference
2.3.7 Metric
2.3.8 Longest Matching
2.4 Static Routing
2.4.1 Introduction to Static Routing
2.4.2 Static Route Configuration
2.5 Default Routes
2.5.1 Introduction to Default Route
2.5.2 Default Route Configuration
2.6 Dynamic Routing
2.6.1 Overview of Dynamic Routing
2.6.2 Dynamic Routing Protocols
2.6.3 Route Recursion
2.6.4 Equal-Cost Route
2.6.5 Floating Route
2.6.6 CIDR (Classless Inter-Domain Routing) and Variable Length Subnet Masking (VLSM)
2.6.7 Route Summarization
2.6.7.1 Summarization and Calculation
2.7 OSPF Basics
2.7.1 Introduction to OSPF (Open Shortest Path First)
2.7.2 Basic OSPF Concepts: Area
2.7.3 Basic OSPF Concepts: Router ID
2.7.4 Basic OSPF Concepts: Cost Value
2.7.5 OSPF Packet Types
2.7.6 Three Types of OSPF Entries
2.7.6.1 OSPF neighbor table
2.7.6.2 LSDB table
2.7.6.3 OSPF routing table
2.7.7 OSPF Working Mechanism
2.7.7.1 Relationships Between OSPF Routers
2.7.8 Process of Establishing an OSPF Adjacency (From Down to Full)
2.7.9 OSPF Network Types
2.7.9.1 Point-to-Point (P2P):
2.7.9.2 Broadcast Multiple Access (BMA):
2.7.9.3 Non-Broadcast Multiple Access (NBMA):
2.7.9.4 Point-to-Multipoint (P2MP):
2.7.10 DR and BDR
2.7.11 OSPF Domain and Single Area
2.7.12 Multi-Area OSPF
2.7.13 Types of OSPF Routers
2.7.14 Basic OSPF Configurations
2.7.15 Basic OSPF Configurations (Subnet masks)
2.7.16 Basic OSPF Configurations (DR and BDR)
2.7.17 Basic OSPF Configurations (Network Types)
2.7.18 Basic OSPF Configurations (Multiple Area)
2.7.19 Basic OSPF Configurations (Hello and Dead timers)
3 Ethernet switching network construction
3.1 Ethernet Protocols
3.2 Collision Domain and CSMA/CD
3.3 Broadcast Domain
3.4 Ethernet Frames
3.5 MAC Address
3.6 Typical Architecture of a Campus Network
3.7 Ethernet Switch
3.8 Working Principles of Switches
3.8.1 MAC Learning and Forward
3.8.2 Flooding
3.8.3 Discarding
3.9 VLAN (Virtual Local Area Network) and Trunk
3.9.1 Basic Concepts of VLAN
3.9.2 VLAN Tag
3.9.3 VLAN Frame
3.9.4 VLAN Assignment Methods
3.9.5 Layer 2 Ethernet Interface Types
3.9.5.1 Access Interface
3.9.5.2 Trunk Interface
3.9.5.3 Hybrid Interface
3.9.6 Basic VLAN and Access Port configurations
3.9.7 Basic Trunk Port configurations
3.9.8 Basic Hybrid Port configurations
3.10 STP (Spanning Tree Protocol)
3.10.1 Layer 2 and Layer 3 Loops
3.10.2 Introduction to STP (Spanning Tree Protocol)
3.10.3 Bridge ID (BID)
3.10.4 Root Bridge
3.10.5 Cost
3.10.6 Root Path Cost (RPC)
3.10.7 Port ID (PID)
3.10.8 Bridge Protocol Data Unit (BPDU)
3.10.9 BPDU Comparison Rules
3.10.10 STP Operations
3.10.10.1 Select a Root Bridge on the Switching Network
3.10.10.2 Selecting a Root Port on Each Non-root Bridge
3.10.10.3 Designated Port Election on Each Link
3.10.10.4 Block non-designated ports
3.10.11 STP Port States
3.10.12 STP Port State Transition
3.10.13 Basic STP Configuration
3.11 RSTP
3.11.1 Disadvantages of STP
3.11.2 Introduction to RSTP
3.11.3 Port Roles in RSTP
3.11.3.1 Alternate Port
3.11.3.2 Backup Port
3.11.4 Edge Port
3.11.5 Port States in RSTP
3.11.5.1 Discarding State:
3.11.5.2 Learning State:
3.11.5.3 Forwarding State:
3.12 VBST (VLAN-based Spanning Tree)
3.13 MSTP (Multiple Spanning Tree Protocol)
3.14 Intelligent Stack (iStack)
3.15 Smart Link
3.16 Inter-VLAN Communication
3.16.1 Using Physical Interfaces on Routers
3.16.2 Using a Router's Sub-interfaces
3.16.3 Layer 3 Switch and VLANIF Interfaces
3.17 Eth-Trunk
3.17.1 Basic Concepts of Eth-Trunk
3.17.2 Manual Mode
3.17.3 LACP (Link Aggregation Control Protocol)
3.17.3.1 System Priority
3.17.3.2 Interface Priority
3.17.3.3 Maximum Number of Active Interfaces
3.17.4 Load Balancing in Eth-Trunk
3.17.5 Configurations of Eth-Trunk
3.17.6 Other configuration commands
3.17.7 More about iStacks and CSS
3.17.8 Recommended Network Architecture
4 Cyber security infrastructure and network access
4.1 ACL (Access Control Lists)
4.1.1 Introduction to ACL (Access Control Lists)
4.1.2 ACL Composition
4.1.2.1 Components of an ACL
4.1.2.2 Wildcards
4.1.3 ACL Classification and Identification
4.1.4 ACL Matching Mechanism
4.1.5 ACL Matching Position
4.1.6 Configurations of Basic ACL
4.1.7 Configurations of Advanced ACL
4.1.8 Configurations of Named ACL
4.1.9 Other configuration commands
4.2.1 AAA Overview
4.2.2 AAA Architecture
4.2.3 Authentication
4.2.4 Authorization
4.2.5 Accounting
4.2.6 AAA Implementation Protocol - RADIUS
4.2.7 AAA Configurations
4.2.8 Configuration Examples
4.3 NAT (Network Address Translation)
4.3.1 Motivation Behind NAT
4.3.2 Private IP Addresses
4.3.3 Static NAT
4.3.3.1 Configuring Static NAT
4.3.4 Dynamic NAT
4.3.4.1 Configuring Dynamic NAT
4.3.5 NAPT (Network Address and Port Translation)
4.3.5.1 Configuring NAPT (Network Address and Port Translation)
4.3.6 Easy IP
4.3.6.1 Configuring Easy IP
4.3.7 NAT Server
4.3.7.1 Configuring NAT Server
5 Network services and applications
5.1 FTP (File Transfer Protocols)
5.1.1 Configuration Commands for FTP
5.1.1.1 Device as FTP Server
5.1.2 Device as FTP Client
5.1.3 Configuring FTP Server and FTP Client
5.2 TFTP (Trivial File Transfer Protocol)
5.2.1 Configuring TFTP Client
5.3 Telnet
5.3.1 Configurations of Telnet
5.4 DHCP (Dynamic Host Configuration Protocol)
5.4.1 Configurations of DHCP (with global pool)
5.4.2 Configurations of DHCP (without global pool)
5.5 HTTP
5.6 DNS
5.7 NTP (Network Time Protocol)
6 WLAN Basic
6.1 Introduction to WLAN (Wireless Local Area Network)
6.1.1 IEEE 802.11, WLAN, and Wi-Fi
6.1.2 Wi-Fi Development Trends in Office Scenarios
6.1.2.1 Phase 1: Initial Mobile Office Era
6.1.2.2 Phase 2: Wireless Office Era
6.1.2.3 Phase 3: All-Wireless Office Era
6.2 Basic Concepts of WLAN
6.2.1 WLAN Devices
6.2.2 Agile Distributed Architecture
6.2.3 CAPWAP (Control And Provisioning of Wireless Access Points)
6.2.4 AP-AC Networking
6.2.4.1 Layer 2 Networking
6.2.4.2 Layer 3 Networking
6.2.4.3 AP-AC Networking Characteristics
6.2.5 AC Connection Mode
6.2.5.1 In-Path Networking
6.2.5.2 Off-Path Networking
6.2.6 Wireless Communications System
6.2.7 Radio Wave
6.2.8 Radio Channel
6.2.9 BSS/SSID/BSSID
6.2.10 Virtual Access Points (VAP)
6.2.11 Extended Service Set (ESS)
6.3 WLAN Fundamentals
6.3.1 WLAN Working Process Overview
6.3.2 WLAN Working Process: Step 1
6.3.3 WLAN Working Process: Step 2
6.3.3.1 WLAN Profiles
6.3.3.1.1 Regulatory Domain Profile
6.3.3.1.2 Radio Profile
6.3.3.1.3 VAP Profile
6.3.3.1.4 SSID Profile
6.3.3.1.5 Security Profile
6.3.3.2 Data Forwarding Mode
6.3.4 WLAN Working Process: Step 3
6.3.4.1 Scanning in Wireless Networks
6.3.4.1.1 Active Scanning
6.3.4.1.2 Passive Scanning
6.3.4.2 WLAN Security Protocols
6.3.4.3 Link Authentication in WLAN
6.3.4.4 Association in WLAN
6.3.4.5 Access Authentication in WLAN
6.3.4.6 STA Address Allocation
6.3.5 WLAN Working Process: Step 4
7 WAN basics
7.1 Introduction to WAN
7.2 WAN Device Roles
7.3 PPP
7.3.1 PPP (Point-to-Point Protocol) Overview
7.3.2 LCP Negotiation Process - Normal Negotiation
7.3.3 LCP Negotiation Process - Parameter Mismatch
7.3.4 LCP Negotiation - Unrecognized Parameters
7.3.5 PPP Authentication Mode
7.3.5.1 PPP Authentication Mode - PAP
7.3.5.2 PPP Authentication Mode - CHAP
7.3.6 NCP Negotiation
7.3.6.1 NCP Negotiation - Static IP Address Negotiation
7.3.6.2 NCP Negotiation - Dynamic IP Address Negotiation
7.4 PPPoE (PPP over Ethernet)
7.4.1 PPPoE Packets
7.4.2 PPPoE Discovery Stage
7.4.3 PPPoE Session Establishment
7.4.4 PPPoE Session Termination Stage
7.4.5 Configuring PPPoE
7.5 MPLS
7.5.1 Traditional IP Routing and Forwarding
7.5.2 MPLS Label-based Forwarding
7.6 Segment Routing
7.6.1 Introduction to Segment Routing
7.6.2 SR Forwarding Implementation
7.6.3 SR Deployment Modes
7.6.4 SR Applications
8 Network management and O&M
8.1 Basic Concepts of Network Management and O&M
8.1.1 Basic Network Management Functions
8.1.2 Network Management Modes
8.1.2.1 Traditional Network Management
8.1.2.2 iMaster NCE-Based Network Management
8.2 SNMP Fundamentals and Configuration
8.2.1 Introduction to SNMP
8.2.2 Typical SNMP Architecture
8.2.3 SNMP Message Exchange
8.2.4 Management Information Base (MIB)
8.2.4.1 Common MIB Objects
8.2.5 Configuring SNMP
8.3 Network Management Based on Huawei iMaster NCE
8.3.1 NETCONF
8.3.1.1 NETCONF Overview
8.3.1.2 NETCONF Advantages
8.3.1.3 YANG Language Overview
8.3.1.4 YANG and XML (1)
8.3.1.5 YANG and XML (2)
8.3.1.6 Telemetry Overview
9 IPv6 basics
9.1 IPv6 Background
9.1.1 IPv4 Status
9.1.2 IPv6 Advantages
9.2 IPv6 Header
9.2.1 Basic IPv6 Header
9.2.2 IPv6 Extension Header
9.3 IPv6 Address
9.3.1 IPv6 Address Abbreviation Specifications
9.3.2 IPv6 Address Classification
9.3.3 IPv6 Unicast Address Format
9.3.4 Common IPv6 Unicast Address - Global Unicast Address (GUA)
9.3.5 Common IPv6 Unicast Address - Unique Local Address (ULA)
9.3.6 Common IPv6 Unicast Address - Link-Local Address (LLA)
9.3.7 IPv6 Multicast Address
9.3.8 Solicited-Node Multicast Address
9.3.9 IPv6 Anycast Address
9.4 Service Process of IPv6 Unicast Addresses
9.5 Neighbor Discovery Protocol (NDP)
9.6 Dynamic IPv6 Address Configuration
9.7 Duplicate Address Detection (DAD)
9.8 Address Resolution in IPv6
9.9 Configuring Basic IPv6 addresses
9.10 Configuring IPv6 Static (Network) Routing
9.11 Configuring IPv6 Static (Host) Routing
9.12 Configuring IPv6 Static (Default) Routing
9.13 Configuring SLAAC
9.14 Configuring DHCPv6
10 SDN and automation basics
10.1 SDN
10.1.1 SDN Origin
10.1.2 Basic Concepts of OpenFlow
10.1.3 Flow Table Overview
10.1.4 Essential Requirements of SDN
10.1.5 SDN Network Architecture
10.1.6 Huawei SDN Network Architecture
10.2 Network Programmability and Automation
10.2.1 Network Automation Tools
10.2.2 Programming-Based Network Automation
10.2.3 Programming Languages
10.3 Python
10.3.1 Python Overview
10.3.2 Python Code Execution Process
10.3.3 Getting Started with Python Code
10.3.3.1 Interactive Mode
10.3.3.2 Script Mode
10.3.4 Code Style Guide for Python
10.3.5 Code Style Guide for Python - Identifier Naming
10.3.6 Code Style Guide for Python - Code Indentation
10.3.7 Code Style Guide for Python - Using Comments
10.3.8 Code Style Guide for Python - Source Code File Structure
10.3.9 Python Functions and Modules
10.3.9.1 Python Functions
10.3.9.2 Python Modules
10.3.9.2.1 Creating and Using Modules
10.3.9.2.2 Module Features
10.3.10 Python Classes and Methods
10.3.10.1 Classes and Objects
10.3.10.1.1 Classes
10.3.10.1.2 Objects
10.3.10.2 Methods
10.3.11 telnetlib
11 Further Reading
11.1 Huawei iMaster NCE
11.1.1 Huawei CloudFabric DCN Autonomous Driving Network Solution
11.1.2 Huawei CloudCampus Autonomous Driving Network Solution
11.1.3 Device Plug-and-Play
11.1.4 Wired and Wireless Convergence
11.1.5 Intelligent Terminal Identification: Ensuring Secure Access
11.1.6 HQoS: User- and Application-Based QoS Policy
11.1.7 AI-Powered Intelligent O&M of Campus Networks
11.1.8 AI-Powered Intelligent Radio Calibration
11.2 NFV
11.2.1 Key NFV Technologies: Virtualization
11.2.2 Key NFV Technology: Cloudification
11.2.3 Introduction to the NFV Architecture
11.2.4 Functional Modules of the NFV Architecture
11.2.5 Huawei's NFV Solution
學員會於課堂內控制 Huawei 器材進行各種實習。
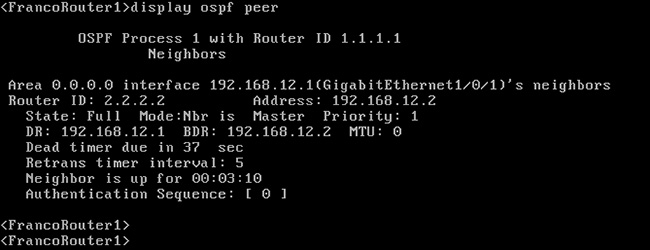
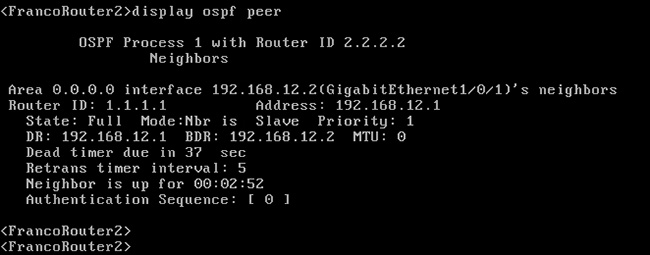
學員會於課堂內使用 Python 等技術進行各種實習。
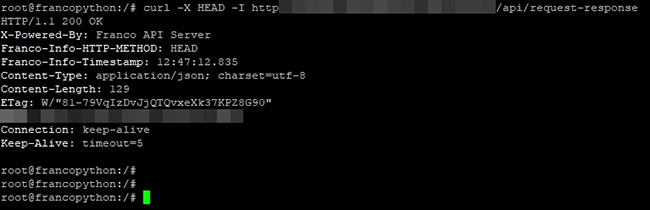
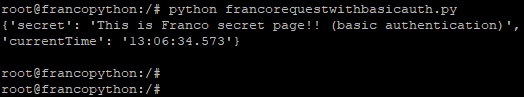
 付款。
付款。