(在家觀看 = 0%,在校觀看 = 100%)
100% 在校觀看日期及時間:
自由選擇,點選以下地區觀看辦公時間及位置
課時: 36 小時
享用時期: 18 星期。進度由您控制,可快可慢。
課堂錄影導師:Larry
在校免費試睇:首 3 小時,請致電以上地點與本中心職員預約。
本課程提供在校免費重睇及導師解答服務。
(在家觀看 = 100%,在校觀看 = 0%)
100% 在家觀看日期及時間:
每天 24 小時全天候不限次數地觀看
課時: 36 小時
享用時期: 18 星期。進度由您控制,可快可慢。
課堂錄影導師:Larry
在校免費試睇:首 3 小時,請致電以上地點與本中心職員預約。
本課程提供導師解答服務。
持有 Azure Solutions 進階級 Architect Expert 國際認可證書的優勢:

- 微軟認為,能考取 Microsoft Certified Azure Solutions Architect Expert 國際認可證書之人士都必然是雲端技術的專家,能設計、管理及保護放置於 Azure Cloud 上的各種各樣的 i.t. 解決方案。
“Microsoft Azure Solutions Architects must have expertise in compute,network,storage,and security so that they can design solutions that run on Azure.” -by Microsoft
- 向世界各地數以百萬計 Azure Cloud 客戶證明您的專業技術水平,加強準僱主對您的信心。
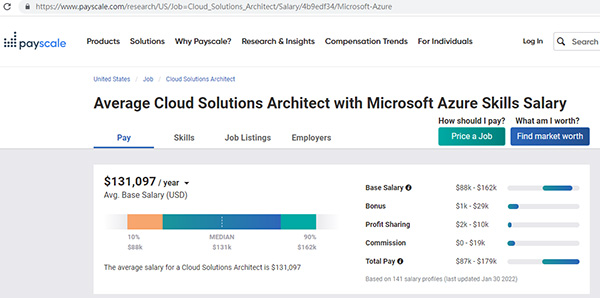
- 於本地某知名求職網站搜尋 “Azure” 或 “Azure Cloud” 等字眼,於香港經常有過百份中至高等雲端工程師職位等您應徵,按您的年資條件,年收入約 $30 萬至 $108 萬港元不等,詳見下圖:
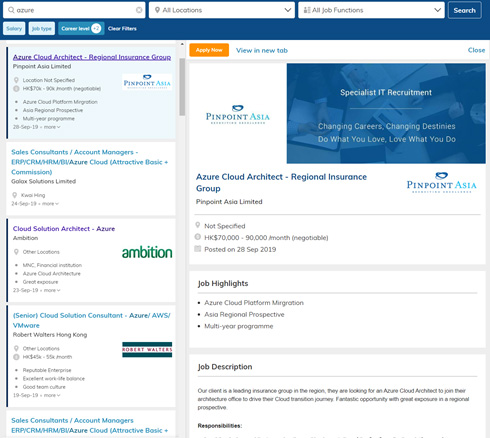
資料來源: https://hk.jobsdb.com/hk/search-jobs/azure/1?Career=3%2C2
而類似 Azure Cloud 職位於歐洲及北美的薪酬比香港更高!
資料來源 Payscale (上圖以美元為年薪單位):
https://www.payscale.com/research/US/Job=Cloud_Solutions_Architect/Salary/4b9edf34/Microsoft-Azure
| 課程名稱: |
Microsoft Certified: Azure Solutions Architect Expert (1科 Azure Cloud) 國際認可證書課程 - 簡稱:Azure Expert Training Course |
| 課程時數: | 36 小時 (共 12 堂,共 1 科) |
| 適合人士: | 已通過 AZ-104 考試人士 |
| 授課語言: | 以廣東話為主,輔以英語 |
| 課程筆記: | 本中心導師親自編寫英文為主筆記,而部份英文字附有中文對照。 |
| 1. 模擬考試題目: | 本中心為學員提供模擬考試題目,每條考試題目均附有標準答案。 |
| 2. 時數適中: | 本中心的 Microsoft Certified Azure Solutions Architect Expert (1 科 Azure Cloud) 國際認可證書課程時數適中,有 36 小時。 令學員能真正了解及掌握課程內容,而又能於短時間內考獲以下 1 張國際認可證書:
|
| 3. 導師親自編寫筆記: | 由本中心已擁有五項 MCITP , 十多項 MCTS,MCSA 及 MCSE 資格,並有教授 Microsoft 相關課程 20年以上經驗的資深導師 Larry Chan 親自編寫筆記,絕對適合考試及實際管理之用,令你無須「死鋤」如字典般厚及不適合香港讀書格調的書本。 |
| 4. 一人一機上課: | 本課程以一人一機模式上課。 |
| 5. 免費重讀: | 傳統課堂學員可於課程結束後三個月內免費重看課堂錄影。 |
Microsoft 已公佈 Microsoft Certified: Azure Administrator Associate 認證持有人 (即已通過入門級 AZ-104 考試的人士) 只要通過以下 1 個 Azure Cloud 相關科目的考試,便可獲發 Microsoft Certified Azure Solutions Architect Expert 國際認可證書:
| 考試編號 | 科目名稱 |
| AZ-305 | Designing Microsoft Azure Infrastructure Solutions |
本中心為Microsoft指定的考試試場。報考時請致電本中心,登記欲報考之科目考試編號、考試日期及時間
(最快可即日報考)。臨考試前要出示身份證及繳付每科HK$943之考試費。 考試不合格便可重新報考,不限次數。欲知道作答時間、題目總數、合格分數等詳細考試資料,可瀏覽本中心網頁 "各科考試分數資料"。 |
|
課程名稱:Microsoft Certified: Azure Solutions Architect Expert (1科 Azure Cloud) 國際認可證書課程 - 簡稱:Azure Expert Training Course |
AZ-305 (36 hours)
1. Design a solution for logging and monitoring
1.1 Introduction to Logging and Monitoring
1.2 Design for Log Analytics
1.2.1 Important considerations for an access control strategy
1.3 Analyze resource utilization and consumption
1.3.1 Configure diagnostic settings on resources
1.3.2 Create baseline for resources
1.3.3 Create and test alerts
1.3.4 Create action groups
1.3.5 Monitor for unused resources
1.3.6 Monitoring and Reporting on Spend
1.3.7 Log Search query functions
1.3.8 Visualize diagnostics data using Azure Monitor Workbooks
1.3.9 Access Control Overview
1.3.10 Scale and ingestion volume rate limit
1.4 Design for Azure Workbooks
1.5 Design for Azure Insights
1.5.1 Application Insights
1.5.2 Azure Monitor VM insights
1.5.3 Azure Monitor container insights
1.6 Design for Azure Data Explorer
1.7 Monitor resources for performance efficiency
1.7.1 Application profiling considerations for performance monitoring
1.7.2 Analyze infrastructure metrics and logs
1.7.3 Performance data integration
2. Design authentication and authorization solutions
2.1 Design for identity and access management
2.2 Design for Azure Active Directory
2.3 Design for Azure Active Directory Business to Business
2.4 Design for Azure Active Directory Business to Customer
2.5 Design for conditional access
2.6 Design for identity protection
2.6.1 User risk policies
2.6.2 Sign-in risk policies
2.6.3 Enabling Azure Active Directory Identity Protection
2.7 Design for access reviews
2.7.1 Determine the purpose of the access review
2.7.2 Determine who will conduct the reviews
2.7.3 Create an access review plan
2.7.4 Create and perform an access review for users
2.8 Design service principals for applications
2.8.1 Design managed identities
2.8.2 What are managed identities in Azure?
2.8.3 When to use managed identities
2.8.4 Vault authentication with managed identities for Azure resources
2.8.5 Select application service principals
2.8.6 Relationship between application objects and service principals
2.8.7 Applications represented in Azure AD
2.8.8 Design a user consent solution for applications
2.8.9 Types of permissions
2.8.10 Effective permissions
2.8.11 Best practices for requesting permissions
2.9 Design for Azure Key Vault
2.9.1 Why use Azure Key Vault?
2.9.2 Design a solution using Keys and SAS tokens
3. Design governance
3.1 Introduction to Design Governance
3.2 Design for management groups
3.2.1 Things to know about management groups
3.2.2 Things to consider when creating management groups
3.3 Design for subscriptions
3.3.1 Things to know about subscriptions
3.3.2 Things to consider when creating subscriptions
3.4 Design for resource groups
3.4.1 Things to know about resource groups
3.4.2 Things to consider when creating resource groups
3.4.3 Design for resource tags
3.4.4 Things to know about resource tags
3.4.5 Things to consider when creating resource tags
3.4.6 Consider the type of tagging that is required.
3.5 Design for Azure policy
3.5.1 Things to know about Azure policy
3.5.2 Things to consider when using Azure policy
3.6 Design for role-based access control
3.6.1 What is Azure role-based access control (RBAC)?
3.6.2 How does role-based access control work?
3.6.3 Things to consider when using role-based access control
3.7 Design for Azure blueprints
3.7.1 How are Azure Blueprints different from Azure Policy
4. Design identities and access for applications
4.1 Integrating all your apps with Azure AD
4.1.1 Use Azure AD for new applications
4.1.2 Determine existing application usage and prioritize work
4.1.3 Integrate apps that rely on other identity providers
4.1.4 Integrate on-premises applications
4.1.5 Integrate apps your developers build
4.2 Permissions and Consent Framework
4.2.1 Understanding permissions and the consent framework in the Microsoft identity platform
4.3 Delegated permissions and consent
4.3.1 Delegated permissions
4.3.2 User consent
4.3.3 Static consent
4.3.4 The /.default scope
4.3.5 Dynamic consent
4.4 Application permissions and consent
4.4.1 Application permissions
4.4.2 Admin consent
4.4.3 Recommended: Sign the user into your app
5. Design a data storage solution for relational data
5.1 Introduction to relational data
5.2 Design for Azure SQL Database
5.2.1 Analyze Azure SQL deployment options
5.2.2 Azure SQL Database
5.2.3 What are SQL elastic pools?
5.2.4 Analyze Azure purchasing models
5.2.5 Analyze Azure database service tiers
5.2.6 An Exercise of creating an Azure SQL Database
5.3 Design for Azure SQL Managed Instance
5.3.1 Azure SQL Managed Instance
5.3.2 Scalability for Azure SQL Managed Instance
5.4 Design for SQL Server on Azure VM
5.4.1 SQL Server on Azure VMs
5.5 Recommend a solution for database scalability
5.5.1 Types of scaling in Azure SQL Database
5.5.2 Design Vertical scaling solution
5.5.3 Design Horizontal Scaling Solution
5.6 Recommend a solution for database availability
5.6.1 General Purpose
5.6.2 Business Critical
5.6.3 Hyperscale
5.6.4 Geo-replication and auto-failover groups
5.7 Design security for data at rest, data in transit, and data in use
5.7.1 Protect data-at-rest
5.7.2 Azure's Azure Key Vault service for TDE
5.7.3 Protect data-in-transit
5.7.4 Protect data-in-use
5.7.5 Always Encrypted feature for data-at-rest and data-in-transit
5.8 Design for Azure SQL Edge
5.8.1 Understand Azure SQL Edge deployment models
5.8.2 How does Azure SQL Edge work?
5.8.3 Scenario - Real time ingestion of data
5.8.4 When do we use Azure SQL Edge?
5.9 Introduction to Cosmos DB
5.10 Key Benefits of Azure Cosmos DB
5.10.1 Turnkey global distribution
5.10.2 Always On
5.10.3 Elastic scalability of throughput and storage, worldwide
5.10.4 Guaranteed low latency at 99th percentile, worldwide
5.10.5 Precisely defined, multiple consistency choices
5.10.6 No schema or index management
5.10.7 Battle tested database service
5.10.8 Ubiquitous regional presence
5.10.9 Secure by default and enterprise ready
5.10.10 Significant TCO savings
5.10.11 Industry leading comprehensive SLAs
5.10.12 Globally distributed operational analytics and AI with natively built-in Apache Spark
5.10.13 Develop applications on Cosmos DB using popular Open Source Software (OSS) APIs
5.10.14 Solutions that benefit from Azure Cosmos DB
5.11 Creating an Azure Cosmos DB Account
5.12 SQL as a JSON Query Language
5.13 Distributing Cosmos DB data globally
5.14 Using Availability Zones to increase redundancy
5.15 Enabling Automatic Failover
5.16 Data Migration Tool
5.17 Cosmos DB Notebook (optional knowledge)
5.18 Design for Azure Cosmos DB and tables
5.19 Differences between Azure Storage tables and Azure Cosmos DB tables
5.20 Other benefits to moving to Cosmos DB
5.21 What database APIs does Cosmos DB provide?
5.21.1 When to use Core (SQL) API
5.21.2 When to use MongoDB API
5.21.3 When to use the Cassandra API
5.21.4 When to use the Gremlin API
6. Design a solution for backup and disaster recovery
6.1 Design for backup and recovery
6.2 Design for Azure Backup
6.2.1 What can you do with Azure Backup?
6.2.2 Where is the data backed up?
6.2.3 Considerations for storage vaults
6.3 Design for Azure blob backup and recovery
6.3.1 Take advantage of blob soft delete and versioning
6.3.2 Consider point-in-time restore for block blobs
6.3.3 Prevent accidental changes by using resource locks
6.4 Design for Azure files backup and recovery
6.4.1 Azure Files provides the capability to take share snapshots of file shares
6.4.2 How can you automate file share backups?
6.4.3 Considerations for file share backups
6.5 Design for Azure virtual machine backup and recovery
6.5.1 How do Azure virtual machines backups work?
6.5.2 Backup policies and retention
6.5.3 Considerations for Azure virtual machine backup and recovery
6.6 Design for Azure SQL backup and recovery
6.6.1 Describe automated backups
6.6.2 Describe backup usage cases
6.6.3 Long-term backup retention policies
6.7 Design for Azure Site Recovery
6.7.1 What can you do with Azure Site Recovery?
6.7.2 Consider using Azure Site Recover with Azure Backup
7. Design for High Availability
7.1 Identify the availability requirements of Azure resources
7.1.1 Workload availability targets
7.1.2 Identify dependencies
7.1.3 Reliability Design Principals
7.1.4 Identify critical system flows
7.1.5 Identify less critical components
7.1.6 Understand service-level agreements
7.2 Design for Azure Front Door
7.2.1 How Azure Front Door works in reliability scenarios
7.2.2 High availability scenarios
7.3 Design for Azure Traffic Manager
7.3.1 How Azure Traffic Manager works in reliability scenarios
7.3.2 High availability scenarios
7.4 Recommend a high availability solution for compute
7.4.1 Design with Azure Availability Zones
7.4.2 When to select virtual machine scale sets
7.4.3 Design a highly available container solution
7.4.4 Describe Azure Storage replication options
7.4.5 Infrastructure-based asynchronous replication
7.4.6 Application-based asynchronous replication
7.4.7 Consider Azure Backup or Velero
7.5 Recommend a high availability solution for relational data storage
7.5.1 General purpose
7.5.2 Business critical
7.5.3 Hyperscale
7.5.4 Database service tiers for availability
7.5.5 Availability Zones
7.5.6 Azure SQL SLA
7.5.7 Active geo-replication
7.5.8 Auto-failover groups
7.5.9 Geo-replication and auto-failover groups
7.6 Recommend a high availability solution for non-relational data storage
7.6.1 Azure storage redundancy
7.6.2 Summary of storage redundancy options
7.6.3 Data Lake Storage redundancy
8. Design for compute solution
8.1 Choosing a compute service
8.1.1 Review the compute hosting options
8.2 Design for Azure virtual machine solutions
8.2.1 Start with the network
8.2.2 Name the virtual machine
8.2.3 Decide the location for the VM
8.2.4 Determine the size of the VM
8.2.5 Review the pricing model
8.2.6 Review the storage options
8.2.7 Select an operating system
8.3 Design for Azure Batch solutions
8.3.1 When to use Azure Batch
8.3.2 How Azure Batch works
8.3.3 Best practices and useful tips for using the Azure Batch service
8.4 Design for Azure App Services solutions
8.4.1 Types of app services
8.4.2 Azure App Service costs
8.4.3 Use App Services deployment slots for continuous deployment
8.4.4 Consider authentication and authorization options
8.4.5 When to use web apps
8.4.6 When to use API apps
8.4.7 When to use WebJobs
8.4.8 When to use Mobile apps
8.5 Design for Azure Container Instances solutions
8.5.1 Container Groups
8.5.2 Security considerations for container instances
8.5.3 When to choose containers instead of virtual machines
8.6 Design for Azure Kubernetes solutions
8.6.1 What is Azure Kubernetes Services (AKS)?
8.6.2 When to use Azure Kubernetes Service
8.7 Design for Azure Functions solutions
8.7.1 What are Azure Functions?
8.7.2 Scenarios for Azure Functions
8.7.3 Best practices and tips for using Azure Functions
8.8 Design for Logic App solutions
8.8.1 How are Azure Logic Apps and Azure Functions different?
8.8.2 Decision criteria for Logic Apps
8.8.3 Summary of design criteria for logic apps
9. Design an Application Architecture
9.1 Describe message and event scenarios
9.1.1 Select messages or events for your application
9.1.2 What is a message?
9.1.3 What is an event?
9.1.4 When should you choose messages or events?
9.2 Design a messaging solution
9.2.1 Azure Queue Storage
9.2.2 Azure Service Bus?
9.2.3 Azure Service Bus Queues
9.2.4 Azure Service Bus publish-subscribe topic
9.2.5 Which messaging service should I choose?
9.3 Design an Event Hubs messaging solution
9.3.1 How Azure Event Hubs works
9.3.2 Considerations for Event Hubs
9.4 Design an event-driven solution
9.4.1 What is Azure Event Grid?
9.4.2 Comparison of services
9.4.3 Use the services together
9.5 Design a caching solution
9.5.1 Recommend a caching solution for applications
9.5.2 Azure Cache for Redis
9.5.3 When to use Azure Cache for Redis?
9.6 Design API integration
9.6.1 Select an API management solution
9.6.2 Azure API Management
9.6.3 When to use Azure API Management?
9.6.4 Consider Azure API Management
9.7 Design an automated app deployment solution
9.7.1 Azure Resource Manager (ARM) templates
9.7.2 What are Bicep templates?
9.7.3 Azure Automation
9.8 Design an application configuration management solution
9.8.1 Azure App Configuration
9.8.2 Development
9.8.3 Production
9.8.4 What are the benefits of App Configuration?
10. Design migrations
10.1 Evaluate migration with the Cloud Adoption Framework
10.1.1 Understand Cloud migration in the Cloud Adoption Framework
10.1.2 Understand the migration effort
10.2 Describe the Azure migration framework
10.2.1 What is the Azure migration framework?
10.2.2 Assess your on-premises environment
10.2.3 Migrate your workloads
10.2.4 Optimize the migrated workloads
10.2.5 Monitor your workloads
10.3 Assess your on-premises workloads
10.3.1 Describe migration tools
10.3.2 Assess your environment
10.4 Select a migration tool
10.4.1 Describe Azure Migrate
10.4.2 What can you do with Azure Migrate?
10.4.3 Migrate web apps to Azure
10.4.4 Migrate VMs with Azure Migrate
10.4.5 Describe Azure Resource Mover
10.5 Migrate your databases
10.5.1 What is the Azure Database Migration Service?
10.5.2 Overview of database migration
10.6 Select an online storage migration tool
10.6.1 Overview of the Windows Storage Migration Service
10.6.2 Migrate data with the Storage Migration Service
10.6.3 Requirements
10.6.4 Use Azure File Sync
10.6.5 What is Azure File Sync?
10.6.6 Azure File Sync terminology
10.7 Migrate offline data
10.7.1 Overview of Azure Import/Export
10.7.2 When to use Azure Import/Export
10.7.3 How Azure Import/Export works
10.7.4 Overview of Azure Data Box
10.7.5 When should you use Data Box?
10.7.6 What are the Data Box components?
10.7.7 How to select between Azure Import/Export and Azure Data Box
11. Design network solutions
11.1 Recommend a network architecture solution based on workload requirements
11.1.1 Gather Network Requirements
11.1.2 Segmentation
11.1.3 Security
11.1.4 Best practice: Plan IP addressing
11.1.5 Best practice: Implement a hub and spoke network topology
11.1.6 Best practice: Design subnets
11.2 Design for on-premises connectivity to Azure Virtual Networks
11.2.1 VPN connection
11.2.2 Azure ExpressRoute connection
11.2.3 ExpressRoute with VPN failover
11.2.4 Hub-spoke network topology
11.2.5 Hub-spoke network topology with Azure Virtual WAN
11.3 Design for Azure network connectivity services
11.3.1 Virtual network
11.3.2 Design network segmentation
11.3.3 Pattern 1: Single virtual network
11.3.4 Pattern 2: Multiple virtual networks with peering in between them
11.3.5 Pattern 3: Multiple virtual networks in a hub & spoke model
11.3.6 Virtual network NAT gateway
11.3.7 Routing
11.3.8 System routes
11.3.9 User defined routes (UDRs)
11.4 Design for application delivery services
11.4.1 Content Delivery Network (CDN)
11.4.2 Azure Front Door Service
11.4.3 Traffic Manager
11.4.4 Load balancer
11.4.5 Application Gateway
11.4.6 Choosing a load balancer solution
11.5 Design for application protection services
11.5.1 Distributed denial of service protection
11.5.2 Azure Private Link
11.5.3 Azure Firewall
11.5.4 Web Application Firewall
11.5.5 Network security groups
11.5.6 Service endpoints
11.5.7 Azure Bastion
11.5.8 Just in time (JIT) network access
11.6 Creating Virtual Network Connectivity in Azure Cloud
11.6.1 Benefits of VNet Peering
11.6.2 Connectivity
11.6.3 Service chaining
11.6.4 Gateways and on-premises connectivity
11.6.5 Lab of Configuring Global VNet Peering
11.6.6 Options for connecting additional virtual networks
11.6.7 Point-to-Site VPN and Certification based authentication
11.6.8 Generating a Client Authentication certificate
11.6.9 Exporting the Root Certificate in BASE64 public key .cer format
11.6.10 Configuring VPN Client Address Pool and Tunnel Type
11.6.11 Uploading trusted Root Certificate
11.6.12 Generate VPN Client packages
11.7 Configuring Azure Site to Site (S2S) VPN
11.7.1 Configuring Site-to-Site Connections in Azure VPN Gateway
11.7.2 Configuring On-Premises VPN device
11.7.3 Verifying Connectivity
11.8 Azure Network Security Groups
11.9 Azure Micro-Segmentation Application Security Groups (ASGs)
11.9.1 Filtering East-West traffic
11.9.2 Filtering north-south traffic
11.10 Implementing Azure Firewall
11.10.1 Creating Subnets for Azure Firewall deployment
11.10.2 Create two more Subnets within the increased address space 10.0.0.0/16
11.10.3 Creating the Jump Virtual machine
11.10.4 Deploying Azure Firewall
11.10.5 Creating a NVA-based default route to redirect traffic
11.10.6 Creating a network rule
11.10.7 Change the primary and secondary DNS address for the Workload’s network interface
11.10.8 Testing the Azure Firewall
11.10.9 Using FQDN Tags in Azure Firewall Rule
 付款。
付款。