(在家觀看 = 0%,在校觀看 = 100%)
100% 在校觀看日期及時間:
自由選擇,點選以下地區觀看辦公時間及位置
課時: 30 小時
享用時期: 10 星期。進度由您控制,可快可慢。
課堂錄影導師:Larry
在校免費試睇:首 3 小時,請致電以上地點與本中心職員預約。
本課程提供在校免費重睇及導師解答服務。
(在家觀看 = 100%,在校觀看 = 0%)
100% 在家觀看日期及時間:
每天 24 小時全天候不限次數地觀看
課時: 30 小時
享用時期: 10 星期。進度由您控制,可快可慢。
課堂錄影導師:Larry
在校免費試睇:首 3 小時,請致電以上地點與本中心職員預約。
本課程提供導師解答服務。
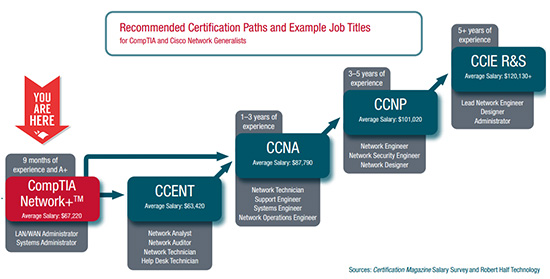
CompTIA (The Computing Technology Industry Association) 於 1982 年成立,其推行的 Network+ 認證是一套中立的 (Vendor Neutral) 國際認證,目的是要確認您擁有建立、管理、保護與優化網絡的能力。

CompTIA
為何要考取 CompTIA Network+ 認證?
- 因其中立的特性,通常成為 I.T. 專業人士首先考取的認證。
- 全球 50 萬人持有,反映其受歡迎程度。
- 根據美國勞工統計局 (Bureau of Labor Statistics) 的分析,網絡管理人員的需求將於 2012 至 2022 年間提升 12%。
- 領先而中立的認證,會被全球各地的國際級機構重視,並被設定為必要的入職條件。例如 Dell、HP、Ricoh、Sharp、Xerox 及 Apple Consultant Network 技術人員便必需持有 CompTIA Network+ 認證。
- 為進修 Cisco、Microsoft、Oracle、IBM 等等更高級的商業認證作準備。
- “Network+ provides a solid foundation for networking professionals to pursue vendor-specific certifications such as the Cisco CCNA” - By Cisco.
| 課程名稱: |
CompTIA Network+ 國際認可證書課程 - 簡稱:CompTIA Network+ Training Course |
| 課程時數: | 合共 30 小時 (共 10 堂),共 1 科 |
| 適合人士: | 有志投身 I.T. 界的人士 |
| 授課語言: | 以廣東話為主,輔以英語 |
| 課程筆記: | 本中心導師親自編寫英文為主筆記,而部份英文字附有中文對照。 |
| 1. 模擬考試題目: | 本中心為學員提供模擬考試題目,每條考試題目均附有標準答案。 |
| 2. 時數適中: | 本中心的 CompTIA Network+ 國際認可證書課程時數適中,有 30 小時。令學員能真正了解及掌握課程內容,而又能於 3 個月內考獲 CompTIA Network+ 國際認可證書。 |
| 3. Larry Chan 親自教授: | Larry 具備了 20 年以上電腦、網絡、數據庫及保安系統的工作經驗,而最近 20 年更於本中心全職教學。 |
| 4. Larry Chan 親身編寫筆記: | Larry 親自編寫筆記,絕對適合考試及實際管理網路之用,令你無須「死鋤」如字典般厚及不適合香港讀書格調的書本。 |
| 5. 一人一機上課: | 本課程以一人一機模式上課。 |
| 6. 免費重讀: | 傳統課堂學員可於課程結束後三個月內免費重看課堂錄影。 |
CompTIA 已公佈考生必須通過以下 1 個 CompTIA Network+ 相關科目的考試,便可獲發 CompTIA Network+ 國際認可證書:
| 考試編號 | 科目名稱 |
| N10-009 | CompTIA Network+ |
本中心為 CompTIA 指定的考試試場。報考時請致電本中心,登記欲報考之科目、考試日期及時間 (最快可即日報考)。臨考試前考生須出示身份證及繳付考試費。 考試編號 N10-009 考試費為 HK$3,198。 |
|
課程名稱:CompTIA Network+ 國際認可證書課程 - 簡稱:CompTIA Network+ Training Course |
N10-009 CompTIA Network+ (30 Hours)
1. Computer Network Basics
1.1 Defining Network
1.1.1 The Purpose of Networks
1.1.2 Overview of Network Component
1.2 Networks Defined by Geography
1.2.1 Local Area Network (LAN)
1.2.2 Wide-area network (WAN)
1.2.3 Campus-area network (CAN)
1.2.4 Metropolitan-area network (MAN)
1.2.5 Personal-area network (PAN)
1.2.6 SANs
1.2.7 SDWANs
1.2.8 MPLS
1.2.9 mGRE
1.3 Networks Defined by Topology
1.3.1 Physical v.s. Logical Topology
1.3.2 Bus Topology
1.3.3 Ring Topology
1.3.4 Star Topology
1.3.5 Hub-and-Spoke Topology
1.3.6 Full-Mesh (完全網狀) Topology
1.3.7 Partial-Mesh Topology
1.3.8 Hybrid Topology
1.3.9 Bringing Wireless to a Topology
1.3.10 Infrastructure Wireless Topology
1.3.11 Ad Hoc Wireless Topology
1.3.12 Wireless Mesh Topology
1.4 Networks Defined by Resource Location
1.4.1 Client/Server Networks
1.4.2 Peer-to-Peer Networks
1.5 Network Links and Concepts
1.5.1 DSL Internet Access
1.5.2 Cable Broadband
1.5.3 The Public Switched Telephone Network
1.5.4 Leased Lines
1.5.5 T3 Lines
1.5.6 Metro-Optical
1.5.7 Satellite Internet Access
1.5.8 Termination Points
1.5.9 Demarc, Demarc Extension, and Smart Jacks
1.5.10 CSUs/DSUs
1.5.11 Verify Wiring Installation and Termination
1.5.12 Virtual Networking
2. Models, Ports, Protocols, and Network Services
2.1 The Purpose of the OSI Reference Model
2.2 The OSI 7-Layer Reference Model
2.3 Layer 1: Physical Layer
2.3.1 How bits are represented on the medium
2.3.2 Wiring standards for connectors and jacks
2.3.3 Physical Topology
2.3.4 Clock Synchronization
2.3.5 Bandwidth usage
2.3.6 Multiplexing Strategy
2.4 Layer 2: Data Link Layer
2.4.1 Media Access Control (MAC)
2.4.2 Logical Link Control
2.5 Layer 3: Network Layer
2.6 Layer 4: Transport Layer
2.7 Layer 5: Session Layer
2.8 Layer 6: Presentation Layer
2.9 Layer 7: Application Layer
2.10 TCP/IP Stack
2.11 Layers in TCP/IP Stack
2.12 Common Applications that uses TCP/IP Stack
2.13 Identifying the OSI Layers at Which Various Network Components Operate
2.14 Data Encapsulation/Decapsulation and OSI
2.15 Ports and Protocols
2.15.1 Connection-Oriented Protocols Versus Connectionless Protocols
2.15.2 Internet Protocol
2.15.3 Transmission Control Protocol
2.15.4 How TCP Works
2.15.5 User Datagram Protocol
2.15.6 Internet Control Message Protocol
2.15.7 IPSec
2.15.8 Generic Routing Encapsulation
2.15.9 File Transfer Protocol
2.15.10 Secure Shell
2.15.11 Secure File Transfer Protocol
2.15.12 Telnet
2.15.13 Simple Mail Transfer Protocol
2.15.14 Domain Name System (DNS)
2.15.15 Dynamic Host Configuration Protocol (DHCP)
2.15.16 Trivial File Transfer Protocol
2.15.17 Hypertext Transfer Protocol
2.15.18 Network Time Protocol (NTP)
2.15.19 Post Office Protocol Version 3/Internet Message Access Protocol Version 4
2.15.20 Simple Network Management Protocol
2.15.21 SNMP Management Systems
2.15.22 SNMP Agents
2.15.23 Management Information Bases
2.15.24 Lightweight Directory Access Protocol
2.15.25 Hypertext Transfer Protocol Secure
2.15.26 Server Message Block
2.15.27 Syslog
2.15.28 SMTP TLS
2.15.29 LDAPS
2.15.30 IMAP over SSL
2.15.31 POP3 over SSL
2.15.32 SQL, SQLnet, and MySQL
2.15.33 Remote Desktop Protocol
2.15.34 Session Initiation Protocol
2.16 Understanding Port Functions
2.17 Network Services
2.17.1 Domain Name Service (DNS)
2.17.2 The DNS Namespace
2.17.3 Types of DNS Entries
2.17.4 DNS Records
2.17.5 DNS in a Practical Implementation
2.17.6 Windows Internet Name Service (WINS)
2.17.7 Dynamic Host Configuration Protocol
2.17.8 The DHCP Process
2.17.9 DHCP and DNS Suffixes
2.17.10 DHCP Relays and IP Helpers
2.17.11 Network Time Protocol
3. Network Components
3.1 Coaxial Cable
3.2 Twisted-Pair Cable
3.3 Shielded Twisted Pair
3.4 Unshielded Twisted Pair
3.5 Connectors
3.6 Plenum (防火夾層) Versus Nonplenum Cable
3.7 Fiber-Optic Cable
3.8 Multimode Fiber
3.9 Single-Mode Fiber
3.10 Fiber Connector Polishing (拋光) Styles
3.11 Media Converters
3.12 Cable Distribution
3.13 Troubleshooting Common Cable Connectivity Issues
3.13.1 Limitations, Considerations, and Issues
3.13.2 Throughput, Speed, and Distance
3.13.3 Cabling Specifications/Limitations
3.13.4 Cabling Considerations
3.13.5 Cabling Applications
3.13.6 Attenuation and dB Loss
3.13.7 Interference
3.13.8 Incorrect Pinout
3.13.9 Bad Ports
3.13.10 Open/Short
3.13.11 LED Status Indicators
3.13.12 Incorrect Transceivers
3.13.13 Duplexing Issues
3.13.14 TX/RX Reversed
3.13.15 Dirty Optical Cables
3.13.16 Common Tools
3.13.17 Cable Crimpers, Strippers, and Snips/Cutters
3.13.18 Punchdown Tools
3.13.19 Tone Generator
3.13.20 Loopback Adapter
3.13.21 Multimeter
3.13.22 Tap
3.13.23 Fusion Splicer (光纖熔接機)
3.13.24 Spectrum Analyzer
3.13.25 Fiber Light Meter
3.14 Wireless Technologies
3.15 Network Infrastructure Devices
3.15.1 Hubs
3.15.2 Bridges
3.15.3 Switches
3.15.4 Multilayer Switches
3.15.5 Routers
3.15.6 Infrastructure Device Summary
3.16 Specialized Network Devices
3.16.1 VPN Concentrators
3.16.2 Firewalls
3.16.3 Proxy Servers
3.16.4 Content Engines
3.16.5 Content Switches
3.17 Virtual Network Devices
3.17.1 Virtual Servers
3.17.2 Virtual Routers and Firewalls
3.17.3 Virtual Switches
3.17.4 Virtual Desktops
3.17.5 Other Virtualization Solutions
3.17.6 Cloud Computing
3.17.7 Software-Defined Networking
3.18 Voice over IP Protocols and Components
4. Ethernet Topology
4.1 Principles of Ethernet
4.2 Ethernet Origins
4.3 Carrier Sense Multiple Access Collision Detect
4.4 Distance and Speed Limitations
4.5 Ethernet Switch Features
4.6 Virtual LANs
4.7 Switch Configuration for an Access Port
4.8 Trunks
4.9 Switch Configuration for a Trunk Port
4.10 Spanning Tree Protocol
4.11 Corruption of MAC Address Table
4.12 Broadcast Storms
4.13 STP Operation
4.14 Link Aggregation
4.15 Power over Ethernet 802.3af
4.16 Port Monitoring
4.17 User Authentication
4.18 Management Access and Authentication
4.19 First-Hop Redundancy
4.20 Miscellaneous Switch Features
5. IPv4 and IPv6 Address
5.1 Structure (結構) of IP Address
5.2 Concept of Binary Number
5.2.1 First Concept of Binary Number:
5.2.2 Second Concept of Binary Number:
5.3 Network ID and Host ID
5.4 Identifying (辨認) the Network ID
5.4.1 Class A
5.4.2 Class B
5.4.3 Class C
5.4.4 Class D
5.4.5 Class E
5.5 重要事實
5.6 更改IP Address的步驟
5.7 Subnet Mask (子網路遮罩)
5.8 Use of Subnet Mask
5.9 Subnetting (子網路化)
5.9.1 Another Example of Subnetting
5.10 Default Gateway
5.10.1 Static Route (靜態路線)
5.10.2 Default Gateway (預設閘口)
5.11 Basic Concepts of IPv6
5.12 The Next Generation TCP/IP stack
5.13 IPv6 Overview
5.13.1 IPv6 Addressing Representation
5.13.2 Compressed IPv6 Format
5.13.3 IPv6 Unicast Address
5.14 Aggregatable Global Address
5.15 Site-Local Address
5.16 Unique-Local Address
5.17 Link-Local Address
6. Basic Concept of Routing
6.1 Concept of the Routing Processes and Sources of Routing Information
6.2 Directly Connected Routes
6.3 Static Routes
6.4 Dynamic Routing Protocols
6.5 Characteristics of Routing Protocol
6.6 IGPs and EGPs
6.7 Method of Routing Information Exchanges
6.7.1 Distance Vector
6.7.2 Link State
6.7.3 IGP Versus EGP
6.7.4 Hybrid Routing Protocols
6.8 Metric Value
6.9 Routing Protocols Example
6.10 Address Translation
6.10.1 Network Address Translation (NAT)
6.10.2 Port Address Translation (PAT)
6.11 Routing for Multicast traffic
6.12 Internet Group Management Protocol (IGMP)
6.12.1 IGMP Version 1 (IGMPv1)
6.12.2 IGMP Version 2 (IGMPv2):
6.12.3 IGMP Version 3 (IGMPv3):
6.13 Protocol Independent Multicast (PIM)
6.13.1 PIM Dense Mode (PIM-DM)
6.13.2 PIM Sparse Mode (PIM-SM)
7. Wireless Solutions
7.1 Introducing Wireless LANs
7.2 WLAN Concepts and Components
7.3 Wireless Routers
7.4 Wireless Access Point
7.5 Antennas
7.6 Frequencies and Channels
7.7 CSMA/CA
7.8 Transmission Methods
7.9 WLAN Standards
7.9.1 802.11a
7.9.2 802.11b
7.9.3 802.11g
7.9.4 802.11n
7.9.5 802.11ac
7.10 802.11 Standard Summary
7.11 Cellular Technology Access
7.12 Speed, Distance, and Bandwidth
7.13 Antenna
7.13.1 Antenna Ratings
7.13.2 Antenna Coverage
7.14 Deploying Wireless LANs
7.14.1 Types of WLANs
7.14.2 IBSS
7.14.3 BSS
7.14.4 ESS
7.14.5 Mesh Topology
7.15 Sources of Interference
7.15.1 Other WLAN devices
7.15.2 Cordless phones
7.15.3 Microwave ovens
7.15.4 Wireless security system devices
7.15.5 Physical obstacles
7.15.6 Signal strength
7.16 Wireless AP Placement
7.17 Securing Wireless LANs
7.17.1 Security Issues
7.17.2 War chalking
7.17.3 Rogue Access Points
7.18 Approaches to WLAN Security
7.18.1 MAC address filtering
7.18.2 Disabling SSID broadcast
7.18.3 Pre-Shared key
7.18.4 IEEE 802.1X
7.19 Security Standards
7.19.1 WEP
7.19.2 WPA
7.19.3 WPA2
7.19.4 WPA3
7.20 Troubleshooting Wireless Issues
7.21 Site Surveys
7.22 Factors Affecting Wireless Signals
7.22.1 Interference
7.22.2 Reflection, Refraction, and Absorption
7.22.3 Troubleshooting AP Coverage
8. Network Optimization
8.1 High Availability (HA)
8.2 High-Availability Measurement
8.3 Fault-Tolerant Network Design
8.3.1 Single points of failure
8.3.2 No single points of failure
8.4 Hardware Redundancy
8.5 Layer 3 Redundancy
8.5.1 First Hop Redundancy Protocols
8.5.2 Layer 3 EtherChannel
8.6 Design Considerations for High-Availability Networks
8.7 High-Availability Best Practices
8.8 QoS Technologies
8.9 Introduction to QoS
8.10 QoS Configuration Steps
8.11 Traffic Components
8.11.1 Best Effort
8.11.2 Integrated Services (IntServ)
8.11.3 Differentiated services (DiffServ)
8.12 QoS Mechanisms
8.12.1 Classification
8.12.2 Marking
8.12.3 Congestion Management
8.12.4 Congestion Avoidance
8.13 Policing and Shaping
8.14 Link Efficiency
9. Networking Command Line Tools
9.1 Windows-based Command Line Tools
9.1.1 ARP
9.1.2 IPCONFIG
9.1.3 NBTSTAT
9.1.4 NETSTAT
9.1.5 NSLOOKUP
9.1.6 PING
9.1.7 ROUTE
9.1.8 TRACERT
9.1.9 PATHPING
10. Network Management
10.1 Maintenance Tools
10.2 Bit-Error Rate Tester
10.3 Butt Set
10.4 Cable Certifier
10.5 Cable Tester
10.6 Connectivity Software
10.7 Electrostatic Discharge Wrist Strap
10.8 Environmental Monitor
10.9 Protocol Analyzer
10.10 WiFi Analyzer/Spectrum Analyzer
10.11 Looking-Glass Sites
10.12 Throughput Tester
10.13 Time Domain Reflectometer/Optical Time Domain Reflectometer
10.14 Monitoring Resources and Reports
10.15 SNMP
10.16 Syslog
10.17 Event Logs
10.18 Application Logs
10.19 Security Log
10.20 System Logs
11. Cloud Computing Concepts and Options
11.1 Service Models
11.1.1 Software as a Service
11.1.2 Platform as a Service
11.1.3 Infrastructure as a Service
11.1.4 Desktop as a Service
11.2 Deployment Models
11.2.1 Private Cloud
11.2.2 Public Cloud
11.2.3 Hybrid and Community Clouds
11.2.4 Infrastructure as Code
11.2.5 Connectivity Options
11.2.6 Multitenancy
11.2.7 Elasticity
11.2.8 Scalability
11.2.9 Security Implications
11.2.10 The Relationship Between Resources
12. Network Operations
12.1 Organizational Documents and Policies
12.2 Wiring and Port Locations
12.3 Troubleshooting Using Wiring Schematics
12.4 Physical and Logical Network Diagrams
12.5 Baseline Configurations
12.6 Policies, Procedures, Configurations, and Regulations
12.6.1 Policies
12.7 Password-Related Policies
12.7.1 Password Policies
12.7.2 Password Strength
12.7.3 Procedures
12.7.4 Change Management Documentation
12.8 Configuration Documentation
12.8.1 Regulations
12.8.2 Labeling
12.9 High Availability and Disaster Recovery
12.9.1 Backups
12.9.2 Full Backups
12.9.3 Differential Backups
12.9.4 Incremental Backups
12.9.5 Snapshots
12.9.6 Backup Best Practices
12.9.7 Using Uninterruptible Power Supplies
12.9.8 Beyond the UPS
12.9.9 Cold, Warm, Hot, and Cloud Sites
12.9.10 High Availability and Recovery Concepts
12.9.11 Active-Active Versus Active-Passive
12.10 Monitoring Network Performance
12.10.1 Introduction
12.10.2 Common Performance Metrics
12.10.3 SNMP Monitors
12.10.4 Management Information Base (MIB)
12.10.5 Network Performance, Load, and Stress Testing
12.10.6 Stress Tests
12.10.7 Performance Metrics
12.10.8 Network Device Logs
12.10.9 Security Logs
12.10.10 Application Log
12.10.11 System Logs
12.10.12 History Logs
12.10.13 Log Management
12.10.14 Patch Management
12.10.15 Environmental Factors
13. Network Attacks and Security
13.1 Network Security Goals
13.2 Confidentiality
13.2.1 Symmetric Encryption
13.2.2 Asymmetric Encryption
13.3 Integrity
13.4 Availability
13.5 Categories of Network Attacks
13.6 Confidentiality Attacks
13.7 Integrity Attacks
13.8 Availability Attacks
13.9 Denial of Service
13.10 TCP SYN Flood
13.11 Buffer Overflow
13.12 ICMP Attacks
13.13 Electrical Disturbances
13.14 Defending Against Attacks
13.15 End User Awareness Training
13.16 Patching
13.17 Security Policies
13.17.1 Governing Policy
13.17.2 Technical Policies
13.17.3 End-User Policies
13.18 Incident Response
13.19 Vulnerability Scanners
13.19.1 Nessus
13.19.2 Network Mapper (NMAP)
13.20 Honey Pots and Honey Nets
13.21 Access Control Lists
13.22 Firewalls
13.23 Firewall Types
13.23.1 Software firewall
13.23.2 Hardware firewall
13.24 Firewall Inspection Types
13.24.1 Packet Filters
13.25 Stateful Firewall
13.26 Firewall Zones
13.27 Unified Threat Management Firewalls
13.28 Virtual Private Networks
13.28.1 Site-to-site VPN
13.28.2 Client-to-Site VPN
13.29 Intrusion Detection and Prevention
13.30 IDS and IPS Device Categories
13.30.1 Policy-Based Detection
13.30.2 Anomaly-Based Detection
13.31 Network-Based and Host-Based Solutions
13.32 Security Information and Event Management
13.33 Common Networking Attacks
13.33.1 Denial-of-Service and Distributed Denial-of-Service Attacks
13.33.2 Types of DoS Attacks
13.34 Vulnerabilities and Prevention
 付款。
付款。